
Lorena Salagre and B. Farias / Noun Project / Via thenounproject.com
You – and just about anyone with an email account – are susceptible to being tricked by what’s called a “phishing” scam, or malicious emails that look genuine. Hacked inboxes aren’t just a problem for political figures like vice president Mike Pence, senior members of Hillary Clinton’s campaign, and French president-elect Emmanuel Macron. Cybercriminals target Internet users of all stripes to gain access to email and other online accounts associated with that email address, like online banking or social media. In fact, these kinds of attacks are so widespread that in a recent consumer alert, the IRS reported a 400% increase in online phishing and malware incidents during the 2016 tax season.
With email hacking methods becoming more sophisticated, it’s important to know how exactly to identify illegitimate emails and what to do if you get tricked. Here’s a guide to everything you need to know to protect yourself from email scams.
What is “phishing”?
No, it is not the act of enjoying the band Phish.
Phishing is a form of social engineering. An email phishing attack is often a message designed to look like it’s from a trusted source when it’s actually not. It can appear to be an email from a colleague asking if you can take a look at a document. It can appear to be an automated message from a service you use, asking you to log in to your account to verify something.
Talented hackers thoughtfully craft their messages to make them look legitimate in order to get victims to give up personal information, click on a link, or download an attachment that may infect their device. To be “phished” usually requires user action. You need to actually do something – like click on a malicious link or attachment – otherwise, it’s just a phishing attempt.
Phishing can also be executed through malicious ads on unsecure websites or links sent through a text message.
Why is it called that?
A quick Google search for “origin of the word phishing” reveals that the term is a portmanteau of the words fishing and phreaking. Fishing refers to using different methods (like emails, advertisements, and links on sites) as lures for account information, like passwords. Phreaking was a term used to describe people who explored, experimented with, and hacked telephone systems in the ‘60s and ‘70s. The most commonly referenced origin story is that the term phishing was created in 1996 by a group of AOL hackers.
What does a phishing email look like?
What makes phishing emails so effective is that they look like normal emails from people you know or organizations you’re familiar with.
“I recently received an email from a lawyer that was completely within the wheelhouse of something he would ask me. It said, ‘Can you take a look at this attachment?’,” recalled Richard Aborn, president of the Citizens Crime Commission of New York City (CCC). That email turned out to be fraudulent.
Aborn stressed that, when analyzing a sketchy email, paying attention to detail is crucial. “I also received an email from American Express that looked so real…but there was a small typo at the bottom.”
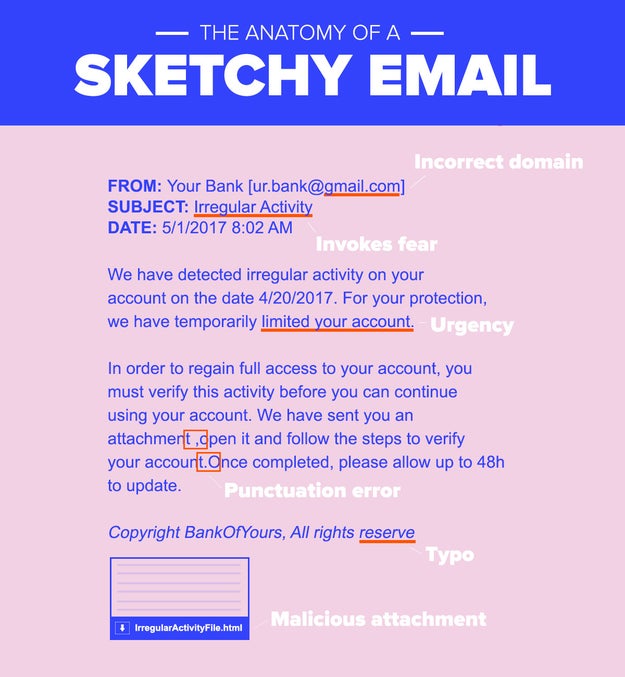
Nicole Nguyen / BuzzFeed News
The CCC, which recently published a report on the state of phishing, provides a great checklist of what to look out for. If you receive a suspicious email, ask yourself these questions:
– The sender: Is the “name” of the sender purporting to be an organization’s, but the sender’s email address domain is gmail.com? Is there a variation in the address’s domain (such as .net or .org, instead of .com)?
– The recipient: Does the email address you by name? If so, is it inaccurate?
– The message: Are there grammatical errors or typos? Does the message’s language sound urgent? Is there a deadline for action?
– Links or attachments: Hover over the hyperlink with your cursor and check if the hyperlinked text and URL match. Is it a sketchy IP address instead of a normal URL? Is it a .exe file (a type of file known to carry viruses)?
If you answered “yes” to one or more of these questions, it’s probably a phishing attempt.
Be extra vigilant about confirming an email's authenticity if it's an email you didn't expect, especially ones requesting sensitive personal information. Asking for things like your password, Social Security number, bank account PIN or credit card number is a telltale sign of fraud.
“A company with good security practices will never ask for your username and password via email,” said security expert Jessy Irwin.
One popular form of phishing is an email from a social media site like Facebook, Instagram, or Twitter, stating that you have become verified or there is an issue with your account because of copyright and threatening deactivation, unless you fill out a form linked in the email.
Another states that your iCloud or Microsoft Outlook account has been suspended or someone has logged in to your account on an unrecognized device. The email will have a link that leads to a website that *looks* like an official Apple or Microsoft page, with fields to submit a username and password, but the URL will look long and spammy.
In more sophisticated attacks, the hacker may already know something about you and use that nugget of information to their advantage. For example, it may appear to be from a friend or colleague and include language like, “Here are pictures from last week.” In one very targeted instance, a hacker breached a major oil company by sending a PDF of a takeout menu for a Chinese restaurant that was popular with employees.
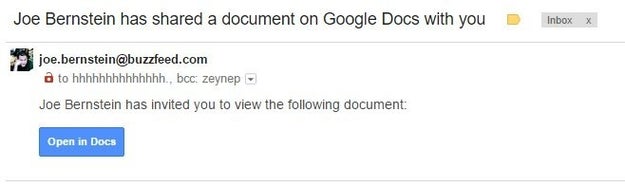
The most recent viral scam, which security experts said was one of the fastest-spread phishing campaigns in history, had someone from a recipient’s address book send an email with the subject “[Name] has shared a document on Google Docs with you.” In the body of the email was an “Open in Docs” link, styled the way a genuine Google Docs email would. Clicking on the link sent the phishing scam to everyone on a victim’s contact list, and granting the app permission gave attackers complete access to their victims’ Google data.
What are some tips for avoiding phishing scams?
The CCC’s Aborn follows this simple rule: “Don’t click until you’re sure. Even if you know the sender.”
You can try verifying links is through a link checker (Norton Safe Web and Phish Tank have free online tools that can help you determine whether or not something is legitimate) – but the easiest, safest thing to do is navigate to the website directly in your browser or contact customer service. If the message purportedly from a colleague or friend, contact them through another method of communication (phone, text, Facebook, IRL, etc.) and ask for verification.
For attachments, don’t download anything that looks suspicious. Microsoft Word documents (which end in .doc or .docx), if opened in Word, have the ability to execute code that can infect your device. Gmail has a built-in anti-virus scanner that allows you to preview PDF or Word documents, and if you open an attached document in “preview mode” (by clicking “View” and not “Download”), you can see the contents of the file without opening the Word or Adobe desktop apps. However, I’d advise you not to even preview the file, even though that is considered less risky than downloading it. A very clever attack replicated the attachment pane in Gmail, and led users to a fake Google sign-in page.
Still, following these authentication steps may not be enough. Some hackers are very, very good at what they do, and even IT professionals have fallen for phishing schemes.
“Many people think that the trick to not getting phished is to spot suspicious emails and attachments 100% of the time, but it is an absolute waste of time to try to become an expert…because attackers are so far ahead of the email counterfeiting game,” Irwin said.
Irwin urges people to be picky about giving any app access to your email. “If you haven't used an app in a long time, or can't remember why you gave it permission to access your inbox, revoke its permissions immediately so that it cannot harvest any of your personal information,” she advised. You can easily revoke apps you don’t recognize or haven’t used in a while with access to Google, if you use Gmail. While you’re at it, check your app integrations with Twitter and Facebook, too.
You should also turn on two-factor authentication everywhere you can (here’s a comprehensive list of websites with two-factor), which requires an additional form of verification so your password isn’t the only way to access an account. However, Irwin notes that, “SMS is an incredibly insecure method for sending an extra factor of authentication.” Instead of text message, she suggests using a code generator app like Google Authenticator or a security key like Yubikey. However, two-factor may not be enough to stump hackers. They might have a copy of your backup codes or physical access to your phone with an authenticator app installed, for example.
“Don’t click until you’re sure. Even if you know the sender.”
Additionally, Irwin recommends using a password manager (like LastPass or 1Password), which can help you avoid being phished online by not auto-populating your username and password unless you’re on the right website. Most managers have browser extensions that automatically fill in your credentials for sites like Gmail or Facebook, and won’t recognize a spammy or fake URL.
Password managers can also help you create super strong, unique passwords for every account, which is *crucial* to protecting your online privacy. According to Brian Krebs, an independent cybersecurity journalist and author of Spam Nation, “most breaches in general – including email account hacking – involve successful phishing attacks. However, credential re-use across multiple sites is also a huge contributor to email account hacks, maybe bigger than phishing.”
What happens if I fall for a phishing scam? How dangerous is it?
Change your password immediately. Then, review the third-party apps you’ve authenticated with your account, and report the phishing attempt to the company the hackers were posing as:
Apple: Report hackers with iCloud, me.com, or mac.com email addresses to abuse@icloud.com and send emails to reportphishing@apple.com.
Facebook: Send emails to phish@fb.com.
Google: Report hackers with Gmail addresses here and emails in Gmail with the down arrow next to Reply > click Report phishing.
Microsoft: In Outlook, click the arrow next to Junk > click Phishing scam. You can also contact the Microsoft Answer Desk.
Amazon: Send emails to stop-spoofing@amazon.com.
Continue to check your login history for your Apple, Facebook, Google, and Microsoft after changing your password to remotely log out of any unrecognized devices, and make sure hackers still don’t have access to your account. There is no way to review where you are logged in with your Amazon account currently, so if your Amazon account is hacked, change your password immediately.
Next, if you are a US resident, file a complaint with the FBI’s Internet Crime Complaint Center. In Canada, reach out to the Anti-Fraud Center, and in the UK, you can report an attack to ActionFraud.
If hackers gain access to your email account, they may be able to reset the password of any account associated with that email address. They may also hold it for ransom and request a sum of money to turn it back over to you. Hackers can also hijack your reputation, by posting content to your social media accounts.
So, yeah, whatever you do: Don’t click if you aren’t sure and don’t re-use passwords!

And don’t just protect your email accounts. “It's really important for people to realize that most of what can happen to them through email can also happen in their text messages and their social media inboxes, too,” Irwin said. “So building good habits for email, if applied to texting and to social media, can help everyone keep it together online.”
Quelle: <a href="It’s Easy To Fall For Email Phishing Scams. Here’s How To Protect Yourself“>BuzzFeed
Published by